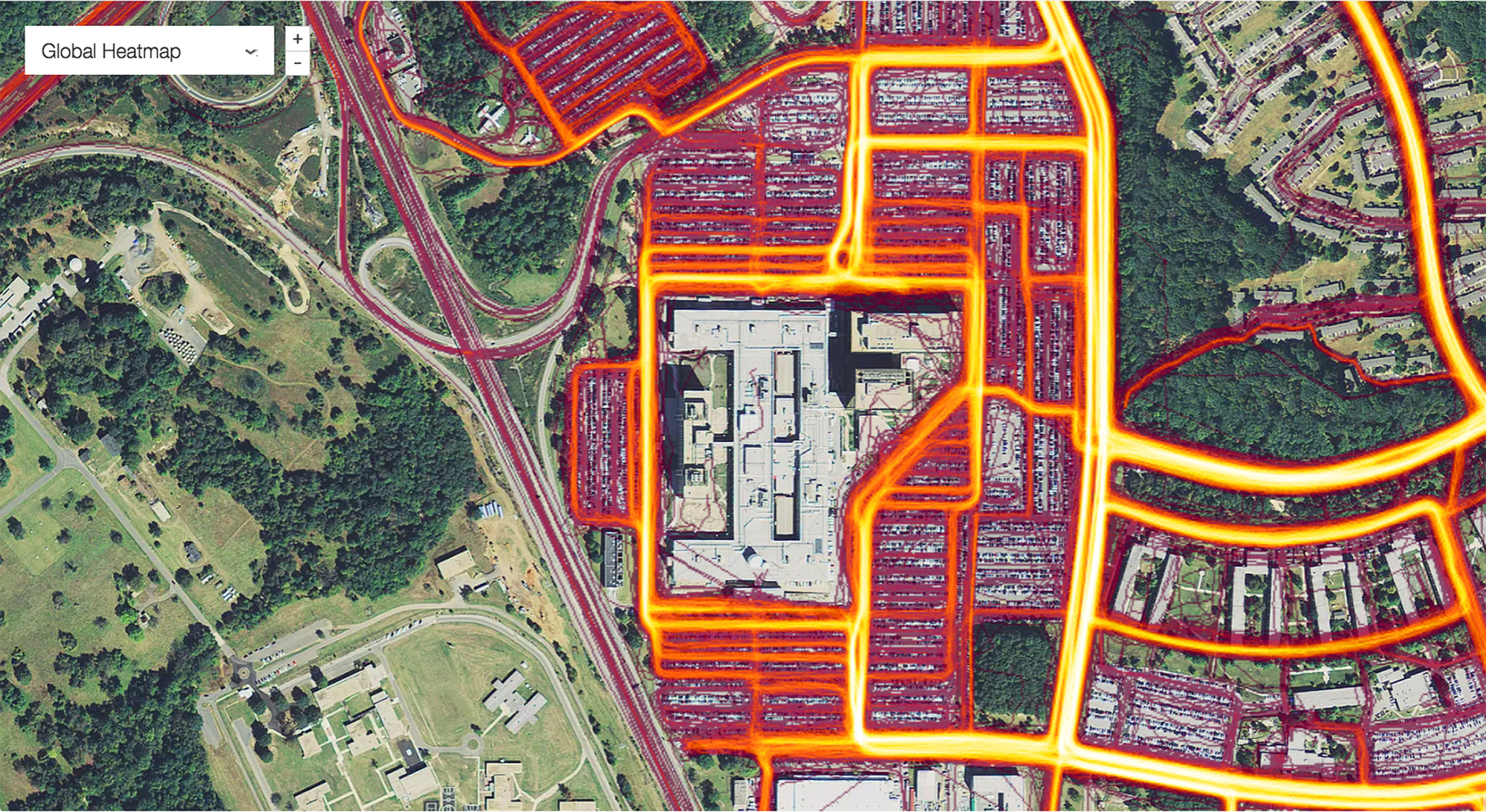
Sensitive information about the locations of U.S. and allied military bases, apparent troop movements, and even data linked to social media profiles has been revealed in a map released by a popular fitness app company.
The Global Heat Map, published by Strava Labs, used GPS satellite information to map the locations and movements of some of the 27 million people who subscribe to its fitness service over a two-year period, between 2015 and September 2017, by illuminating areas of activity.
The map, released last November but only publicized over the weekend, shows all activities ever uploaded to Strava — more than 3 trillion individual GPS data points, according to a blog posting by the company.
















With your current subscription plan you can comment on stories. However, before writing your first comment, please create a display name in the Profile section of your subscriber account page.